No Description
For those that don’t know what recon is, it is pretty much what you would call information gathering. You always do recon when you first do a pentest to get a scope of your target. In that way, the more information you have, the better ways you can exploit weaknesses, whether the weakness is a phishing attack or some physical penetration test. In this question we have to do some Reconnaissance on Julian Cohen. First thing we do? Google
The first thing that pops up is his Twitter
Looking through his tweets we slowly find the answer.
https://twitter.com/HockeyInJune/status/641716034068684800
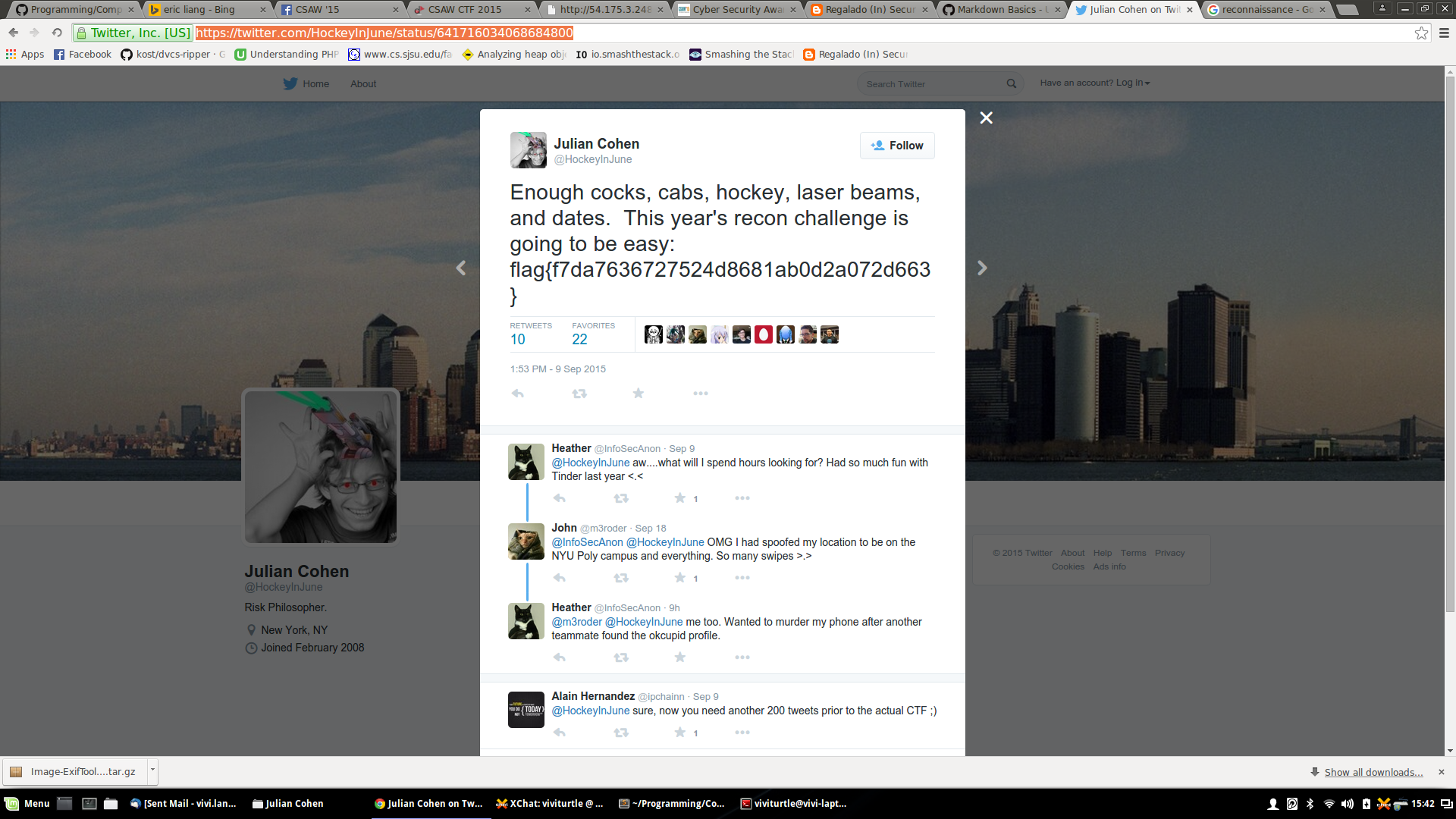
flag{f7da7636727524d8681ab0d2a072d663}